Insights
What is phishing? How this cyber attack works and how to prevent it.
Phishing is a method of trying to gather personal information such as account credentials, financial information or customer data using deceptive e-mails.
Phishing Definition
“Phish” is pronounced how it’s spelled, the same as the word “fish”- the analogy is of an angler throwing a baited hook out there (a phishing email) and hoping you bite.
Phishing is a cyber attack whereby attackers disguise themselves as a trustworthy source and make contact via email. The goal is to trick the recipient into believing that the message is something they need to do, such as: a request for bank details, or a note from someone in their company to click a link or download an attachment, or suspicious activity on their account and a link to change the password.
What distinguishes a phishing attack is the form the messages take. The attacker masques as a trusted entity of some kind, often a real or plausibly real person, or a company the recipient might do business with. It is one of the oldest types of cyberattacks, dating back to the 1990s, and is becoming increasingly sophisticated year on year.
Scammers have become increasingly good at crafting their emails.
Most attackers have now moved to phishing because it’s easy. If they can convince you to give them your credentials, it’s done. There’s nothing more they need- hackers don’t break in, they log in. The vast majority of breaches are the result of stolen passwords, not high-tech hacking tools.
These hackers attack every 39 seconds, on average 2,444 times a day and this has only worsened since the pandemic. Cyber criminals exploited and continue to exploit the spread of COVID-19 and in one week Google saw more than 18 million daily malware and phishing emails related to COVID-19.
As phishing has become more profitable, hackers are becoming increasingly sophisticated in the methods they use to steal passwords, according to Tanmay Ganacharya, a director in Microsoft’s Security Research team. It has reached a point that some IT professionals have even been fooled by them and were unable to spot the subtle differences between a scam email impersonating a CEO and an email from the CEO himself. If an IT professional can be fooled, what hope is there for someone from the accounting office who has little understanding of cybersecurity?
How to spot a Phishing Email
Below is an example of a phishing email, that from an initial glance looks convincing.
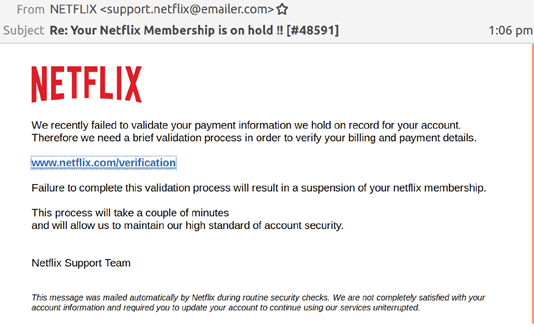
The verification link in the email takes users to a fake Netflix sign in page where hackers harvest the credentials of unsuspecting subscribers. A warning is also presented that warns users that a failure to complete the process will result in their membership being suspended.
As a precaution, ALWAYS avoid clicking links in emails that:
- Are not addressed to you by name, have poor English or omit personal details that a legitimate sender would not include
- Are from businesses you’re not expecting to hear from
- Ask you to download any files
- Take you to a landing page or a website that does not have the legitimate URL of the company the email is claiming to be sent from
- Have an overcomplicated email address or an address that does not have the business name as the @. For example, emails from anyone at razorblue would only come from an @razorblue.com email address.
Protecting your business
The detrimental effects of these crimes costs businesses millions and mean many never recover. Attackers are smarter, more convincing and one method of protection is not enough to fully safeguard your business.
The most effective and secure protection includes:
- Email Security
An effective email security software such as Mimecast should protect against all internal and external email threats and safeguard your business against anti-virus/ anti-spam, email continuity, email security (impersonation protection, detailed attachment scanning) and email archiving.
- Multi-Factor Authentication
MFA is an authentication method which provides any type of business account with a second layer of security. Rather than just a username and password, MFA asks for a unique code which is sent to another one of your devices, ensuring that only authorised personnel can access the business account and operate within the corporate network. - Anti-Virus
Using a number of efficacious anti-virus products will provide your business with leading protection against evolving cyber threats and viruses that are aiming to hack into your organisations confidential data. - Next Generation Firewalls
These give you visibility, control and protection of the traffic flowing through your network, even if its encrypted.
If you have any concerns over the security of your business during these times, please do not hesitate to get in touch.